Ulcer disease or gastritis is a disease that occurs in stomach disorders. Gastric acid levels in a long time will be at risk Causes Ulcer Disease occurs in gastritis or gastric ulcer so that the patient will experience pain in the stomach and midriff is usually accompanied by heartburn and sore.
Pain and tenderness the coming suddenly and spontaneously disappear instantly. Gallstones or kidney stones that cause the disease stopped abruptly. Heartburn is often found in the community, this is the case because of his wrong tend to set the time and eating right.
The cause of ulcer disease are as follows:
1. Fried Food
Most foods that contain very high oil contained fat. To that end, ulcer disease may appear to someone who often consume fried foods.
2. Eating Disorders
If you've been eating lunch and always without breakfast, or also often eat one time a day or wait time is hungry can cause this disease to come.
3. Caffeine
Caffeine as we know it can be soothing, but if too often consumed without eating rice, then the stomach will usually sounds like hunger.
Aside from the food above, there are a few more one cause of heartburn among others such as: stress, flow, lack of sleep, smoking. Ulcer disease can come on when the patient is not timely meal. Some ulcer medications you can make a lot of heartburn relievers, but the core of this drug is to neutralize stomach acid so that no buildup of stomach acid in the stomach wall.
Drugs that could be How to Overcome Disease heartburn is as follows:
=> Cimetidine
=> Antacids
=> Proton pump inhibitors
=> Pankreatin
=> Ranitidine
=> Cytoprotective Agent
If you do not have too much money and still want to use a natural remedy. Please read the following way.
1. How First
Prepare 2 fingers then wash with clean saffron, turmeric grated and added boiled water, squeezed using a clean cloth, the results of juice left in place and take the clear water, or you can also drink straight.
Drink 2 times a day ie morning before meals and at night before bed.
2. Both Ways
Take 8 pieces of guava leaves are still fresh. Then boiled with 1.5 liters of water to a boil, then strain the water grab. Drinks 3 times a day, ie morning, noon, and evening.
3. The Third Way
Prepare turmeric 2 forefinger or in accordance with the needs that you will drink. Then the saffron shredded. Boiled with 2 cups water until the remaining 1 cup or adjust as needed with a ratio of 2: 1. Then filtered and cooled water that has been boiled saffron earlier. Drink 2 times a day ie morning before meals and at night before bed. But, if you got the honey. Should add honey to add better results.
When the drug above have no effect on your Ulcer Disease, please visit the doctor to know more details of your heartburn problems, Causes and How to Overcome Ulcer Disease we have discussed above, and please note that heartburn can not be cured. So, avoid the problems that can cause an ulcer come.
Causes and How to Overcome Ulcer Disease
Causes and How to Overcome Ulcer Disease
IMPORTANT POINTS IN WEB SECURITY
IMPORTANT POINTS IN WEB SECURITY
1. Remote File Inclusion (RFI)
Remote File Inclusion (RFI) is the most frequent type of vulnerabilities found on the website, allowing the attacker to include a file that typically remotely through a script on a web server. The vulnerability occurs because of the use of user input without proper validation. This can lead to something minimal output file contents, but depending on the severity, to list a few that could lead to:
* Code execution on the web server
* Code execution on the client-side as Javascript that can cause other attacks such as cross site scripting (XSS).
* Denial of Service (DoS)
* Data Theft / Manipulation
In PHP main cause is due to the use of unvalidated external variables such as $ _GET, $ _POST, $ _COOKIE with the filesystem functions, most notably include and require statements. Most of the vulnerabilities can be attributed to novice programmers not familiar with all the capabilities of the PHP programming language. PHP language has allow_url_fopen directive and when activated allows the filesystem to use the URL function that allows them to retrieve data from a remote location. An attacker would change the variable passed to one of these functions causes it to insert malicious code from remote resources. To overcome this, all user input must be validated before use.
2. Local File Inclusion (LFI)
The method utilizes the PHP script weaknesses include (), include_once (), require (), require_once () the variable was not declared perfectly.
With LFI an attacker can including the files located on the server in question.
3. SQL injection
SQL injection is a code injection technique that exploit security flaws that occur at the application layer database. The vulnerability is present when user input is not really well screened to avoid character string literals embedded in SQL statements or user input is not strongly typed and thereby unexpectedly executed. This is an instance of a more general class of vulnerabilities that can occur whenever one programming or scripting language is embedded inside another. SQL injection attacks are also known as SQL insertion attacks.
4. Cross Site Scripting (XSS)
Cross-site scripting (XSS) is a type of computer security vulnerability typically found in web applications which allow a malicious attacker to inject a client-side script into web pages viewed by other users. An exploited cross-site scripting vulnerability could be used by attackers to bypass access control policies such as the origin of the same. Cross-site scripting is done on the Web site is about 80% of all security vulnerabilities documented by Symantec in 2007. The impact varied, ranging from minor annoyances to significant security risks, depending on the sensitivity of the data handled by the vulnerable site, and the nature of any security mitigation implemented by the site owner.
Cross-site scripting hole is the weakness of web applications that allow attackers to bypass client-side security mechanisms normally imposed on web content by modern browsers. By finding ways of injecting malicious script into a web page, an attacker can gain access rights be appointed to a sensitive page content, session cookies, and other information that is managed by the browser on the user name. Cross-site scripting attacks therefore a special case code injection.
The expression "cross-site scripting" originally refers to the act of loading applications, third-party web attacked from a site unrelated attack, in a way that executes a JavaScript fragment composed by attackers in the security context of the targeted domain (a reflected or non- persistent XSS vulnerabilities). This definition has gradually expanded to include other modes of code injection, including vectors persistent and non-JavaScript (including Java, ActiveX, VBScript, Flash, HTML or even pure), causing confusion for newcomers in the field of information security.
Various Operating System
Various Operating System
In the world of information systems, does not escape us in trouble operating system or operating system as we know it, as usual that often we know the OS windows which are often used by the public, from children to adults. In the next chapter I will discuss a wide range of Operating Systems, it may not be completely operating system I mentioned in this chapter, but at least I will discuss at least!
Previously I will first discuss what the understanding of the operating system, the operating system is a set of programs that manage computer hardware resources, and provide common services for application software.
WINDOWS OS
Windows OS was first released in November 1985 with the name Windows 1:01, the second release in November 1987 under the name Windows 2:03, followed by Windows 2:10 in may 1988, and Windows 2:11 on March 1989, in Windows 1990 may re-released Windows version 3.0 before the release of Windows 3.1x in March 1992, be followed in the same year in October 1992 released Windows Workgroups version 3.1 on Windows, after the release of the Windows workgroup version 3.1, also released Windows NT version 3.1 back in july 1993, the year 1993 december windows release version of Windows For Workgroups 3.11. Dilanjuti in 1994 Windows 3.2 (released in simple Chinese version) re-released, until the release version of Windows 7 and Windows 8 October 2009 until now.
LINUX OS
LINUX Operating System, is based on three LINUX Operating System before developing other Linux versions are Debian, Slackware and RedHat. Linux version is actually very much because it is an Open Source Operating System.
COMPARISON OF OPERATING SYSTEM WINDOWS AND LINUX
Kernel, whereas Windows has a Linux kernel has a kernel Hybrid Monolithic with modules. License, Windows relying commercial license while Linux license free. GUI, Windows and Linux comparison in terms of GUI that Windows has a GUI ON, while Linux DEPEND.
Other Operating Systems
1. MAC
2. Chrome OS
3. IBM
4. HAIKU
5. RISC OS
6. Morph OS
7. MS DOS
etc.
Previously I will first discuss what the understanding of the operating system, the operating system is a set of programs that manage computer hardware resources, and provide common services for application software.
WINDOWS OS
Windows OS was first released in November 1985 with the name Windows 1:01, the second release in November 1987 under the name Windows 2:03, followed by Windows 2:10 in may 1988, and Windows 2:11 on March 1989, in Windows 1990 may re-released Windows version 3.0 before the release of Windows 3.1x in March 1992, be followed in the same year in October 1992 released Windows Workgroups version 3.1 on Windows, after the release of the Windows workgroup version 3.1, also released Windows NT version 3.1 back in july 1993, the year 1993 december windows release version of Windows For Workgroups 3.11. Dilanjuti in 1994 Windows 3.2 (released in simple Chinese version) re-released, until the release version of Windows 7 and Windows 8 October 2009 until now.
LINUX OS
LINUX Operating System, is based on three LINUX Operating System before developing other Linux versions are Debian, Slackware and RedHat. Linux version is actually very much because it is an Open Source Operating System.
COMPARISON OF OPERATING SYSTEM WINDOWS AND LINUX
Kernel, whereas Windows has a Linux kernel has a kernel Hybrid Monolithic with modules. License, Windows relying commercial license while Linux license free. GUI, Windows and Linux comparison in terms of GUI that Windows has a GUI ON, while Linux DEPEND.
Other Operating Systems
1. MAC
2. Chrome OS
3. IBM
4. HAIKU
5. RISC OS
6. Morph OS
7. MS DOS
etc.
Open Source in Windows I
Open Source in Windows I
Are in the Windows operating system or application software acquired open source that can be used? sometimes often we get from some lay people who asked such a way, the answer is yes there is. Examples such as:
1. Open Office
2. GIMP
3. Octave
4. R
5. And others
HISTORY OPEN OFFICE
First, open office is an office suite, a rival to Microsoft Office, is based on a code of StarOffice is an office suite developed by StarDivision, and was acquired by Sun Microsystems in August, 1994, was acquired by Oracle in 2010, is released as a source projects Opening in July 2000, is available under two different software license is LGPL and SISSI; from version 2.0, he's only available under the LGPL, and software project called "Open Office", was changed to "OpenOffice.org" abbreviated OOO.
Features
1. Can run on multiple platforms, including Windows, Solaris, Linux and Mac OS X.
2. Supports ODF document format (Open Document Files) as an open office suite.
3. Open and save documents in Microsoft Office format
4. Export documents in PDF format
Application:
=> OpenOffice Writer
=> OpenOffice Calc
=> OpenOffice Impress
=> OpenOffice Base
=> OpenOffice Draw
=> OpenOffice Math
What are they looking for?
=> We are looking for people to:
=> Give feedback (input / sarah).
=> Writing or updating documentation.
=> Helping new users.
=> Recommending the project to others.
=> Testing code and report if there are any bugs or errors.
=> Fix an error or bug.
=> Providing advice to a particular feature (under development).
=> Writing and updating software.
=> Creating artwork.
=> Translating into various languages.
=> Whatever you see that need your help.
Comparison with MS.Office
=> Free and Pay
=> OpenOffice little bit slow if you have to open a complex document that uses Microsoft format
=> OpenOffice supports the old computer
=> OpenOffice is available as a portable application
=> Security: depending on the operating system
HISTORY GIMP
=> The GNU Image Manipulation Program (GIMP) is software for raster-based image manipulation
=> Running the GNOME desktop and
=> Released under the GNU GPL license
=> GIMP was originally developed for the X11 desktop running on the UNIX platform
=> It has been ported to some other operating system platforms that MS Windows and Mac OS
=> Graphics generated by the GIMP are stored with XCF format and can be exported to various image formats such as bmp, jpg, gif, pdf, png, svg, tiff, and many others
=> GIMP provides a lot of plugins that make it easier to process the image (image) quickly
Features
=> As a program for coloring
=> Expert quality photo retouching program
=> An online application for batch processing system
=> A product for image renderer
=> An application image format converter and much more
=> In addition, GIMP also provides export / import Photoshop files. So it can edit the image files that have been created in the windows
Specifications Gimp
=> File size: 11.6MB (download), 18-36MB (attached)
=> Publisher: PortableApps.com and GIMP team
=> Date update: 15 July 2007
=> Operating systems: Windows, Linux and others
=> License: free / open source GPL
1. Open Office
2. GIMP
3. Octave
4. R
5. And others
HISTORY OPEN OFFICE
First, open office is an office suite, a rival to Microsoft Office, is based on a code of StarOffice is an office suite developed by StarDivision, and was acquired by Sun Microsystems in August, 1994, was acquired by Oracle in 2010, is released as a source projects Opening in July 2000, is available under two different software license is LGPL and SISSI; from version 2.0, he's only available under the LGPL, and software project called "Open Office", was changed to "OpenOffice.org" abbreviated OOO.
Features
1. Can run on multiple platforms, including Windows, Solaris, Linux and Mac OS X.
2. Supports ODF document format (Open Document Files) as an open office suite.
3. Open and save documents in Microsoft Office format
4. Export documents in PDF format
Application:
=> OpenOffice Writer
=> OpenOffice Calc
=> OpenOffice Impress
=> OpenOffice Base
=> OpenOffice Draw
=> OpenOffice Math
What are they looking for?
=> We are looking for people to:
=> Give feedback (input / sarah).
=> Writing or updating documentation.
=> Helping new users.
=> Recommending the project to others.
=> Testing code and report if there are any bugs or errors.
=> Fix an error or bug.
=> Providing advice to a particular feature (under development).
=> Writing and updating software.
=> Creating artwork.
=> Translating into various languages.
=> Whatever you see that need your help.
Comparison with MS.Office
=> Free and Pay
=> OpenOffice little bit slow if you have to open a complex document that uses Microsoft format
=> OpenOffice supports the old computer
=> OpenOffice is available as a portable application
=> Security: depending on the operating system
HISTORY GIMP
=> The GNU Image Manipulation Program (GIMP) is software for raster-based image manipulation
=> Running the GNOME desktop and
=> Released under the GNU GPL license
=> GIMP was originally developed for the X11 desktop running on the UNIX platform
=> It has been ported to some other operating system platforms that MS Windows and Mac OS
=> Graphics generated by the GIMP are stored with XCF format and can be exported to various image formats such as bmp, jpg, gif, pdf, png, svg, tiff, and many others
=> GIMP provides a lot of plugins that make it easier to process the image (image) quickly
Features
=> As a program for coloring
=> Expert quality photo retouching program
=> An online application for batch processing system
=> A product for image renderer
=> An application image format converter and much more
=> In addition, GIMP also provides export / import Photoshop files. So it can edit the image files that have been created in the windows
Specifications Gimp
=> File size: 11.6MB (download), 18-36MB (attached)
=> Publisher: PortableApps.com and GIMP team
=> Date update: 15 July 2007
=> Operating systems: Windows, Linux and others
=> License: free / open source GPL
Open Source In Windows II
Open Source In Windows II
goodnight lovers of open source, continue the previous discussion that I was posting titled Open Source on Windows. This time I will proceed further material of the same title, only some content just me change it. Okay, this time I will be posting materials on Open Source in Windows II.
Examples of applications that we often find on Open Source as follows among others such as Mozilla Firefox which rivals such as Internet Explorer, Mozilla Thunderbird with rival Microsoft Outlook, VLC with rival Windows Media Player, File Zilla, Celestia, Pigdin and Enigma.
MOZILLA FIREFOX
Is a global community working together since 1998 to build a better Internet. Mozilla Firefox is also a non-profit organization dedicated to promoting openness, innovation and opportunity in the virtual world. Additionally, Mozilla Firefox is an open source project with a variety of software that has been used to build some of the best internet applications.
Features
1. Written using programming language C / C ++, Java script, CSS, XUL, XBL.
2. Can be used on a variety of operating systems.
3. Machine: GeckoSize
4. File size:
1. 15 MB for Windows,
2. 31 MB for Mac OS X,
3. 17 MB for Linux,
4. 75 MB for the source code.
5.Include in 90 even more languages.
Mozilla Firefox vs. Internet Explorer
1. Mozilla Firefox is a free software, while Internet Explorer paid.
2. Mozilla Firefox support multiple operating systems, while IE is only for Windows OS.
3. Mozilla Firefox support MathML, while IE does not support MathML.
4. Mozilla Firefox support but not all XHTML mobile profile, while IE is not.
5. and others
MOZILLA THUNDERBIRD
Is a free email client developed by the Mozilla Foundation, was first known on 28 July 2003.
Features
=> Written using C ++ programming language, XUL, XBL, Javascript, CSSO.
=> Support for multiple operating systems.
=> There is in 53 languages.
=> License: Free.
=> Easy to use where there are features assistant.
=> Tabs search: To perform a search.
=> Multi tab to read the email.
=> Smart folders to organize email.
=> Spam filter.
=> Automatic Update.
Mozilla Thunderbird vs. Microsoft Outlook
Mozilla thunderbird licensors are free / open Sorce, while MS.Outlook is paid or known commercially.
Mozilla Thunderbird supports multiple operating systems, while MS.Outlook can only be used on Mac and Windows operating systems.
Mozilla Thunderbird supports java script, while MS.Outlook unknown.
etc.
VLC
VLC, or known as video lan is a software or application is free and open source, it can be used on multiple platforms multimedia player and framework, running a variety of multimedia files, such as DVDs, Audio CDs, VCDs and various streaming protocols.
Features
=> Simple, powerful and fast.
=> Can run any file, disc, webcam and streams.
=> Can run more codec to not require a codec pack
=> Full
=> As media converters and streamer.
=> And others.
only this that I can say in this chapter, more and less I apologize and thank you for this material and wait for further material!
Examples of applications that we often find on Open Source as follows among others such as Mozilla Firefox which rivals such as Internet Explorer, Mozilla Thunderbird with rival Microsoft Outlook, VLC with rival Windows Media Player, File Zilla, Celestia, Pigdin and Enigma.
MOZILLA FIREFOX
Is a global community working together since 1998 to build a better Internet. Mozilla Firefox is also a non-profit organization dedicated to promoting openness, innovation and opportunity in the virtual world. Additionally, Mozilla Firefox is an open source project with a variety of software that has been used to build some of the best internet applications.
Features
1. Written using programming language C / C ++, Java script, CSS, XUL, XBL.
2. Can be used on a variety of operating systems.
3. Machine: GeckoSize
4. File size:
1. 15 MB for Windows,
2. 31 MB for Mac OS X,
3. 17 MB for Linux,
4. 75 MB for the source code.
5.Include in 90 even more languages.
Mozilla Firefox vs. Internet Explorer
1. Mozilla Firefox is a free software, while Internet Explorer paid.
2. Mozilla Firefox support multiple operating systems, while IE is only for Windows OS.
3. Mozilla Firefox support MathML, while IE does not support MathML.
4. Mozilla Firefox support but not all XHTML mobile profile, while IE is not.
5. and others
MOZILLA THUNDERBIRD
Is a free email client developed by the Mozilla Foundation, was first known on 28 July 2003.
Features
=> Written using C ++ programming language, XUL, XBL, Javascript, CSSO.
=> Support for multiple operating systems.
=> There is in 53 languages.
=> License: Free.
=> Easy to use where there are features assistant.
=> Tabs search: To perform a search.
=> Multi tab to read the email.
=> Smart folders to organize email.
=> Spam filter.
=> Automatic Update.
Mozilla Thunderbird vs. Microsoft Outlook
Mozilla thunderbird licensors are free / open Sorce, while MS.Outlook is paid or known commercially.
Mozilla Thunderbird supports multiple operating systems, while MS.Outlook can only be used on Mac and Windows operating systems.
Mozilla Thunderbird supports java script, while MS.Outlook unknown.
etc.
VLC
VLC, or known as video lan is a software or application is free and open source, it can be used on multiple platforms multimedia player and framework, running a variety of multimedia files, such as DVDs, Audio CDs, VCDs and various streaming protocols.
Features
=> Simple, powerful and fast.
=> Can run any file, disc, webcam and streams.
=> Can run more codec to not require a codec pack
=> Full
=> As media converters and streamer.
=> And others.
only this that I can say in this chapter, more and less I apologize and thank you for this material and wait for further material!
LINUX
LINUX
LINUX OPERATING SYSTEM
Linux is an operating system for PCs, notebooks and others working in multitasking and multi-user.
Advantages of Using Linux
=>Multitasking is able to run commands simultaneously and accsess hardware simultaneously.
=>Namely multi user operating system at the same time can be used by more than one user is entered into the system
=>Virtual memory, linux can utilize the space on the disk to be used as virtual memory, a program which is not active in RAM will be stored on the hard drive.
=>Share Reader, Every command on Linux shared use of a library function, it is useful to save memory.
=>Linux is portable (not dependent on specific hardware), so it can be used ranging from notebook platforms to super computers.
=>Compatibility with IEEE POSIX.1, Standard makes linux supports many standards used by other UNIX operating systems.
=>The price is relatively lower.
=>Support in the form of the free software GNU software.
One derivative Linux
Ubuntu, Ubuntu is one Linux distribution based on Debian and has a graphical desktop interface. Ubuntu project is sponsored by Canonical Ltd (owned by Mark Shuttleworth Company).
Ubuntu History
Ubuntu is a South African ethical ideology centered on community loyalty and relationship between each other.
The word ubuntu comes from ZULU and XHOSA. Installed in a traditional African concept, is regarded as one of the founding principles of the new republic of South African and connected with the idea of the revival of Africa.
A short translation of the word ubuntu is "flavor to humanity towards others". Another translation is "the belief in a universal bond of sharing that connects all humanity".
Ubuntu excellence
Ubuntu is a complete Linux-based operating system, freely available and have good support from the community as well as from professional experts.
Ubuntu community is formed based on the ideas contained in the philosophy of Ubuntu:
That software should be available free of charge.
That software tools should be available in different languages each area and for those who have to limitation physical and financial.
That any person or user should have the freedom to change the software what they need.
These freedoms make Ubuntu different from other software that is proprietary or commercially. Not only free, but also gets the right to modify the software according to user needs.
Just so my material for this, I thank you!
Linux is an operating system for PCs, notebooks and others working in multitasking and multi-user.
Advantages of Using Linux
=>Multitasking is able to run commands simultaneously and accsess hardware simultaneously.
=>Namely multi user operating system at the same time can be used by more than one user is entered into the system
=>Virtual memory, linux can utilize the space on the disk to be used as virtual memory, a program which is not active in RAM will be stored on the hard drive.
=>Share Reader, Every command on Linux shared use of a library function, it is useful to save memory.
=>Linux is portable (not dependent on specific hardware), so it can be used ranging from notebook platforms to super computers.
=>Compatibility with IEEE POSIX.1, Standard makes linux supports many standards used by other UNIX operating systems.
=>The price is relatively lower.
=>Support in the form of the free software GNU software.
One derivative Linux
Ubuntu, Ubuntu is one Linux distribution based on Debian and has a graphical desktop interface. Ubuntu project is sponsored by Canonical Ltd (owned by Mark Shuttleworth Company).
Ubuntu History
Ubuntu is a South African ethical ideology centered on community loyalty and relationship between each other.
The word ubuntu comes from ZULU and XHOSA. Installed in a traditional African concept, is regarded as one of the founding principles of the new republic of South African and connected with the idea of the revival of Africa.
A short translation of the word ubuntu is "flavor to humanity towards others". Another translation is "the belief in a universal bond of sharing that connects all humanity".
Ubuntu excellence
Ubuntu is a complete Linux-based operating system, freely available and have good support from the community as well as from professional experts.
Ubuntu community is formed based on the ideas contained in the philosophy of Ubuntu:
That software should be available free of charge.
That software tools should be available in different languages each area and for those who have to limitation physical and financial.
That any person or user should have the freedom to change the software what they need.
These freedoms make Ubuntu different from other software that is proprietary or commercially. Not only free, but also gets the right to modify the software according to user needs.
Just so my material for this, I thank you!
Database Systems - Entity Relationship Diagram (ERD)
Database Systems - Entity Relationship Diagram (ERD)
Database Systems discussion this time about the Entity Relationship Diagram (ERD) one form of modeling databases are often used in the development of information systems. Discussion includes: Understanding ERD, ERD notations, methods ERD, ERD stage, cardinality, and Case ERD.
Understanding ERD
In software engineering, an Entity-Relationship Model (ERM) is an abstract and conceptual representation of the data. Entity-Relationship modeling method is one of the data base used to generate the conceptual scheme for the type / semantic data model system. Where the system often have a relational database, and its provisions are top-down. The diagram to illustrate the model is called the entitiy-Relationship-Relationship diagrams entitiy, ER diagrams, or ERD.
ERD notation
There are a number of conventions on ERD notation. Classical notation is often used for conceptual models. Various other notations are also used to describe logically and physically from a database, one of which is IDEF1X.
Symbolic notations used in the Entity Relationship Diagram is as follows:
Entity, is everything that can be described by the data. Entities can also be interpreted as an individual representing something real (existence) and can be distinguished from something else (Fathansyah, 1999). There are two kinds of entities, namely a strong entity and the entity is weak. Strong entity is an entity that does not have a dependency with other entities. Examples entity members. While the weak entity is an entity whose occurrence depends on the existence of other entities in a relation.
Attribute, Attributes is a description of the characteristics of the entity. Attributes depicted in the form of a circle or ellipse. Key attributes of the entity or the key is underlined.
Relations or relations, relations indicate a relationship between the number of entities that come from a different set of entities.
Liaison between the relationship set and the entity set entity set with attributes expressed in the form of a line.
Degree relatives or cardinality
Indicates the maximum number of entities that can relate to entities on the set of another entity. Various cardinality is:
One-to-one (one to one), each member of the entity A may only be associated with one member of the entity B, and vice versa.
One to many (one to many), each member of the entity A may be associated with more than one member of the entity B but not vice versa.
Many to many (many to many), each entity A may be associated with many entities entity set B and vice versa.
ERD stage
The first stage in the design of information systems using the ER model is to describe information needs or the type of information to be stored in the database. Data modeling techniques can be used to describe any ontology (ie an overview and classification of terms used and the relationship of information) for a particular region.
The next stage is called logical design, where data is mapped to the logical data model, such as the relational model. Loguis data model is then mapped into the physical model, so that sometimes, the second phase is referred to as "physical design".
In general methodology ERD as follows:
Sample Case:
A company has several parts. Each piece has at least one supervisor and employee. Employee assigned at least one section (may also in some parts). At least one employee has the task in one project. But the holiday and an employee can not be the task in the project.
Determining entity
Entity: supervisor, parts, employees, projects
Determining the relationship with matrix relation
ERD images while
Connect entities in accordance with the relation matrix created
Filling cardinality
From the description of the problem can be seen that:
each section has only one supervisor
a supervisor on duty in one piece
each section there is at least one employee
each employee working at least in one part
each project undertaken by at least one employee
determine the key
The key point: The number of Trustees, Section Name, Employee Number, Project Number.
Drawing ERD based key
There are two many-to-many relationships in the ERD interim, between sections with employees, employees with a project, therefore we create a new entity that is part -pegawai and employee-project A key element of the new entity is the primary key of another entity that will be the key Guests in the new entity.
Specify attributes
Required attributes are: name section, the project name, employee name, supervisor name, project number, number of employees, number of inspectors
Mapped attributes
Section: Section name
Project: Project name
Employees: employee name
Supervisor: Name of supervisor
Project-Employee: Number of projects, number of employees
Supervisor: Number watchdog
Drawing ERD with attributes
Checking Results
Check if there are still redundasi. ERD end: for modeling data on the system.
Understanding ERD
In software engineering, an Entity-Relationship Model (ERM) is an abstract and conceptual representation of the data. Entity-Relationship modeling method is one of the data base used to generate the conceptual scheme for the type / semantic data model system. Where the system often have a relational database, and its provisions are top-down. The diagram to illustrate the model is called the entitiy-Relationship-Relationship diagrams entitiy, ER diagrams, or ERD.
ERD notation
There are a number of conventions on ERD notation. Classical notation is often used for conceptual models. Various other notations are also used to describe logically and physically from a database, one of which is IDEF1X.
Symbolic notations used in the Entity Relationship Diagram is as follows:
Entity, is everything that can be described by the data. Entities can also be interpreted as an individual representing something real (existence) and can be distinguished from something else (Fathansyah, 1999). There are two kinds of entities, namely a strong entity and the entity is weak. Strong entity is an entity that does not have a dependency with other entities. Examples entity members. While the weak entity is an entity whose occurrence depends on the existence of other entities in a relation.
Attribute, Attributes is a description of the characteristics of the entity. Attributes depicted in the form of a circle or ellipse. Key attributes of the entity or the key is underlined.
Relations or relations, relations indicate a relationship between the number of entities that come from a different set of entities.
Liaison between the relationship set and the entity set entity set with attributes expressed in the form of a line.
Degree relatives or cardinality
Indicates the maximum number of entities that can relate to entities on the set of another entity. Various cardinality is:
One-to-one (one to one), each member of the entity A may only be associated with one member of the entity B, and vice versa.
One to many (one to many), each member of the entity A may be associated with more than one member of the entity B but not vice versa.
Many to many (many to many), each entity A may be associated with many entities entity set B and vice versa.
ERD stage
The first stage in the design of information systems using the ER model is to describe information needs or the type of information to be stored in the database. Data modeling techniques can be used to describe any ontology (ie an overview and classification of terms used and the relationship of information) for a particular region.
The next stage is called logical design, where data is mapped to the logical data model, such as the relational model. Loguis data model is then mapped into the physical model, so that sometimes, the second phase is referred to as "physical design".
In general methodology ERD as follows:
Sample Case:
A company has several parts. Each piece has at least one supervisor and employee. Employee assigned at least one section (may also in some parts). At least one employee has the task in one project. But the holiday and an employee can not be the task in the project.
Determining entity
Entity: supervisor, parts, employees, projects
Determining the relationship with matrix relation
ERD images while
Connect entities in accordance with the relation matrix created
Filling cardinality
From the description of the problem can be seen that:
each section has only one supervisor
a supervisor on duty in one piece
each section there is at least one employee
each employee working at least in one part
each project undertaken by at least one employee
determine the key
The key point: The number of Trustees, Section Name, Employee Number, Project Number.
Drawing ERD based key
There are two many-to-many relationships in the ERD interim, between sections with employees, employees with a project, therefore we create a new entity that is part -pegawai and employee-project A key element of the new entity is the primary key of another entity that will be the key Guests in the new entity.
Specify attributes
Required attributes are: name section, the project name, employee name, supervisor name, project number, number of employees, number of inspectors
Mapped attributes
Section: Section name
Project: Project name
Employees: employee name
Supervisor: Name of supervisor
Project-Employee: Number of projects, number of employees
Supervisor: Number watchdog
Drawing ERD with attributes
Checking Results
Check if there are still redundasi. ERD end: for modeling data on the system.
Conversion Video MP4 to MP3 in Ubuntu
Conversion Video MP4 to MP3 in Ubuntu
The strength of Linux is on its command-line. Philosophy was actually realized in many ways, because the command-line is more than just a black screen dos-prompt belonging OS next door neighbor. We can do many things with a command-line Linux, ranging from installing programs, setting up the system, making modifications desired files, to convert multimedia, and any other needs. Not just "clever" do a lot of things, a command-line Linux is also further simplify all the processes work.
A small example, this article will discuss how to convert various video MP4 multimedia files into MP3 audio. Many ways we can do, but I will explain the easiest way to do it via the command-line Linux is the name of the program could be "terminal" or "console".
Open Terminal, check whether we have installed "ffmpeg" or not. Type "ffmpeg". If not installed, it will exit the suggestions statement to install. Install the program "ffmpeg" with the tools that are needed as follows. Type in the Terminal:
XCrash @ Ubuntu: / home / bugtraq $ sudo apt-get install ffmpeg libavcodec-extra-53 libav-tools
Then click "Enter", and enter the password (keywords) your root, and then click "Enter" again. Wait until the installation process is complete. Next, you need to know where the location of the file you want to convert. If you have found, please type the following command in the Terminal:
"$ Ffmpeg -i -f namafile.mp4 mp3 -ab 192 000 -vn namaoutput.mp3"
Specification:
ffmpeg = application used to convert
Options -i = explain where the location of your files (input)
video.mp4 = the name of the video file you want to convert. You can use the full path in this section, and do not forget the option the video file name must match the name of the video file on your computer. For example, the video file you want to convert named "radiohead.mp4" and there in the video folder on the home belonging to MEDIA, then writing the full path as follows: /media/MEDIA/video/radiohead.mp4
-f Option mp3 = (format) notify the application that the ffmpeg conversion result is to mp3 format.
-ab Option 192000 = notify the application that we want results ffmpeg conversion (output) encoded to 192kbps (one of the standard formats MP3 encode)
Options -vn = confirmed to ffmpeg that we do not need a "video content" her.
music.mp3 = last command to create an MP3 file name to be created. Please adjust its name with your needs. The MP3 file after completion will be in the same folder as the source MP4 files.
How? Very easy is not it? Nothing is easy for people who do not want to learn. Good luck!
The dangers of smooks for computer
The dangers of smooks for computer
Goodnight lovers computers that do not have a spouse. On this occasion I would like to express my irritation about my lover who has just stricken because of a serious injury to the skin because of a cigarette on a smooth skin that my laptop sticker which became scorched because I smoke near my sweetheart Compaq laptop yaiu 320 of my most dear. This way I had the idea to do the dangers of smoking to health posts computer you all, O my idiot friend. Namely as follows:
1. The dangers of cigarettes can cause your computer sick like blisters on the skin smooth.
2. Bahya cigarettes can also cause your computer to impotence.
3. Smoking also makes your computer barren.
4. For cigarettes, the computer you are experiencing dizziness.
5. Caused by smoking, your computer can not breathe normally as usual.
6. Danger cigarettes can also cause your computer with cancer.
7. Smoking can also cause your computer to crash pregnancy
8. Smoking unwittingly may also cause disturbances in fetal your computer.
9. Smoking can also cause reduced sperm on the laptop.
10. What is even more dangerous, namely, cigarettes can cause your computer breasts become deflated.
From several sources who had ane survey, it causes a danger of smoking on your computer that is a loss of consciousness of the author of this blog or the author of this blog being an idiot. Therefore, stay away from your cigarette on the computer and your laptop! This is the advice of the author of the blog, if you do not stay away from cigarettes from the computer and your laptop, then you will not experience a bad thing. Hopefully my advice work and good day to you all. Good night!
1. The dangers of cigarettes can cause your computer sick like blisters on the skin smooth.
2. Bahya cigarettes can also cause your computer to impotence.
3. Smoking also makes your computer barren.
4. For cigarettes, the computer you are experiencing dizziness.
5. Caused by smoking, your computer can not breathe normally as usual.
6. Danger cigarettes can also cause your computer with cancer.
7. Smoking can also cause your computer to crash pregnancy
8. Smoking unwittingly may also cause disturbances in fetal your computer.
9. Smoking can also cause reduced sperm on the laptop.
10. What is even more dangerous, namely, cigarettes can cause your computer breasts become deflated.
From several sources who had ane survey, it causes a danger of smoking on your computer that is a loss of consciousness of the author of this blog or the author of this blog being an idiot. Therefore, stay away from your cigarette on the computer and your laptop! This is the advice of the author of the blog, if you do not stay away from cigarettes from the computer and your laptop, then you will not experience a bad thing. Hopefully my advice work and good day to you all. Good night!
Basic Of Linux
Basic Of Linux
Objective:
• Knowing about the definition, history and Linux versions
• Knowing comparison of Linux with other Operating Systems
• Knowing the structure of Linux
1.1 What is Linux?
Linux is the name of an operating system (operating system) for the PC that works Multitasking and MultiUser. Linux works in multi-tasking means it can run multiple applications simultaneously, for example, can play games while downloading from the Internet. Linux works in multiuser means Linux supports the use of the application or computer to serve multiple users at once, such a program can be used together on a network line.
Linux is actually a clone (clone) of UNIX that are designed to run on PCs. Talk about UNIX, basically the operating system is portable (not dependent on specific hardware) that can be used ranging from supercomputers to notebook platforms. Similarly, Linux, the operating system is already very popular and much in demand by professionals.
On the other hand UNIX is a commercial operating system that is expensive. UNIX initially created for large computers such as mainframes and supercomputers. UNIX version for PC is a further modification of the original version. Because the version of UNIX to a PC typically requires large computer specifications and momboroskan hard drive space, making it less efficient UNIX to a PC. This makes UNIX clone for the PC platform, including Minix and Linux.
As an operating system, Linux has a variety of uniqueness and advantages that are not owned by other operating systems. And the most typical Linux is a Free software.
1.2 The development of history and Linux Version
Linux itself is derived from the name of the creator of the beginning, Linus Torvalds, which actually refers to a complete set of software which together with the kernel compile a complete operating system. Linus Torvalds created inspired by Minix - a simple UNIX clone system that made Andy Tanenbaum.
Linux operating system environment includes hundreds of programs, including compilers, interpreters, editors and utilities. Assistive devices that support connectivity, ethernet, SLIP and PPP and interoperability. Reliable software product (reliable), including the latest development version. Group of developers spread around the world who have worked and make Linux portable to a new platform, as well as supporting the user community who have diverse needs and also users can participate act as its own developer team.
1.3 The fundamental difference Linux
One thing that distinguishes Linux to other operating systems is price. Linux is cheaper and can be copied and redistributed without having to pay a fee or royalty to someone. But there are other things more important in addition to price considerations, namely the source code. Linux source code is available to all
people so that everyone can get involved directly in its development. This freedom has allowed hardware vendors make driver for a particular device without having to obtain a license source code that is expensive or menandatanganiNon Disclosure Agreement (NDA). And it also has to provide the possibility for everyone to look into a real operating system and commercial quality. Because Linux is freely available on the internet, various vendors have made a distrbusi package which can be regarded as a packaged version of Linux. This package includes the complete Linux environment, the software for installation and may include specialized software and dedicated support.
1.4 Comparison of Linux to other operating systems
Linux is based on POSIX operating system standard that actually derived based on the work function of UNIX. UNIX is compatible with Linux at the system call level, this means that the majority of programs written for UNIX or Linux can be recompiled and run on other systems with minimal changes. Generally speaking, Linux runs faster than other Unix on the same hardware. And again UNIX has a weakness that is not free.
MS-DOS has similarities with Linux is a file system that is hierarchical. But MS-DOS can only run on x86 processor and does not support multi-user and multi-tasking, as well as non-free. MSDOS also do not have good support in order to interoperate with other operating systems, including the unavailability of network software, program developers and utility programs that exist in Linux. C Compiler uses gcc from the Free Software Foundation's GNU Project. The compiler is widely used in the environment Hewlett-Packard and Sun. Nowadays, a lot of Linux applications that can be used for office purposes such as for spreadsheets, word processor, database and graphics editor program that has the function and look like Microsoft Office, that Star Office. In addition, Corel version is also available for Linux and applications like Matlab on Linux known as Scilab. Linux can be found in a variety of distribution (often called distributions). Distro is a bundle of the Linux kernel, along with a basic Linux system, the installation program, basic tools, and other programs that are useful in accordance with the purpose of making distributions.
There are so many Linux distributions, including:
RedHat, the most popular distributions, minimal in Indonesia. RedHat is the first distribution installation and easy operation.
Debian, the distribution that promotes stability and reliability, even at the expense aspects of ease and sophistication of the program. Debian uses the .deb package installation program.
Slackware, an ever dominate distribution in the Linux world. Almost all Linux documentation is based on Slackware. Two important things on Slackware is that all its content (kernel, library or application) is already proven. So it may be a bit old but certainly stable. The second because he advocated for installing from source so that every program that we install optimized with our system. It's the reason he did not want to use the binary RPM and up to Slackware 4.0, it still uses the libc5 not glibc2 like the others.
SuSE, the distribution of which is very famous with YaST (Yet another Setup Tools) to configure the system. SuSE is the first distribution in which the installation can use the Indonesian language.
Mandrake, RedHat distro is a variant optimized for Pentium. If we use a pentium computer up, generally Linux can walk faster with Mandrake.
WinLinux, distributions are designed to be installed on top of the DOS partition (WIndows). So to run it can be clicked from Windows. WinLinux made as if it is an application program under Windows. And many other distros that are already available or will appear.
1.5 Advantages of Linux
Here are described some advantages of the operating system Linux / UNIX compared to other operating systems. And the following are some of the facts of the things that benefit by using the programs and files of Linux / UNIX:
Basically, all the data stored in the hard disk even if there are some conditions where data is stored on a floppy disk.
Linux / UNIX provides some special process where terminals, printers and other hardware devices can be accessed as we access files stored on the hard disk or diskette.
When the program starts, the program is run from the hard disk into RAM and after the run will be named as the process.
Linux / UNIX provides service to create, modify programs, processes and files.
Linux / UNIX supports hierarchical file structure.
Linux / UNIX operating system is one that belongs to the class of operating systems that can perform multitasking. Multitasking itself is a state in which an operating system can do a lot of work at the same time.
In addition to multitasking, Linux / UNIX also supports multiuser. Namely the operating system at the same time can be used by more than one user is entered into the system. Even for Linux also supports to multiconsole where at the same time in front of computers directly without having to go through the network and allows more than one user entered into the system dakam.
Section 1.6 operating system
Operating System Linux / UNIX consists of the kernel, system program and several application programs. The kernel is the core of the operating system that regulates the use of memory, input output devices, processes, user files on the file system and others. The kernel also provides a set of services that are used to access the so-called kernel system call. System call is used to implement the various services required by the operating system.
System program and all other programs that run on top of the kernel is called user mode. The fundamental difference between the system program and application programs are programs that the system needed an operating system can be run while the application program is a program that is needed to run a particular application.
Example: daemon is a system and word processing program (word processor) is an application program.
1.7 Structure software linux
a. Kernel
The kernel is the most important part of the operating system Linux, which serves as the controller hardware and formed various functions at a low level. The kernel also in the service date, time, file management, security surveillance, process scheduling, memory management, system management, and error handling and intrupsi. Linux kernel consists of several important parts, such as process management, memory management, hardware device drivers, file system drivers, network management and others. But the most important part is the process management and memory management. Memory management to handle local memory consumption, swap area, parts of the kernel and for the buffer cache. Management process to handle the manufacturing processes and scheduling processes. At the base of the kernel contains a hardware device
b. Shell
Shell can be said as a translator in linux which serves to menyembatani between users of the system, meaning that the user simply provides the command and the shell will handle the next action. There is a built-in commands and external commands, built-in command is an internal command being owned by the shell itself being an external command, was the internal shell command outside the command itself. This command can be either utility or application program. There are three types of shell, among others bourne shell program name is sh, C program named csh shell, and Korn shell program called ksh.
c. Utilities
Utilities are small programs that are used to carry out certain tasks. Among others: to process files and directories, editor, communications and networking, system administration, analyzing the work system and others.
d. Program applications
Is a program that is ready to be used by users to meet their own needs. These programs are made with high tinggkat programming language.
• Knowing about the definition, history and Linux versions
• Knowing comparison of Linux with other Operating Systems
• Knowing the structure of Linux
1.1 What is Linux?
Linux is the name of an operating system (operating system) for the PC that works Multitasking and MultiUser. Linux works in multi-tasking means it can run multiple applications simultaneously, for example, can play games while downloading from the Internet. Linux works in multiuser means Linux supports the use of the application or computer to serve multiple users at once, such a program can be used together on a network line.
Linux is actually a clone (clone) of UNIX that are designed to run on PCs. Talk about UNIX, basically the operating system is portable (not dependent on specific hardware) that can be used ranging from supercomputers to notebook platforms. Similarly, Linux, the operating system is already very popular and much in demand by professionals.
On the other hand UNIX is a commercial operating system that is expensive. UNIX initially created for large computers such as mainframes and supercomputers. UNIX version for PC is a further modification of the original version. Because the version of UNIX to a PC typically requires large computer specifications and momboroskan hard drive space, making it less efficient UNIX to a PC. This makes UNIX clone for the PC platform, including Minix and Linux.
As an operating system, Linux has a variety of uniqueness and advantages that are not owned by other operating systems. And the most typical Linux is a Free software.
1.2 The development of history and Linux Version
Linux itself is derived from the name of the creator of the beginning, Linus Torvalds, which actually refers to a complete set of software which together with the kernel compile a complete operating system. Linus Torvalds created inspired by Minix - a simple UNIX clone system that made Andy Tanenbaum.
Linux operating system environment includes hundreds of programs, including compilers, interpreters, editors and utilities. Assistive devices that support connectivity, ethernet, SLIP and PPP and interoperability. Reliable software product (reliable), including the latest development version. Group of developers spread around the world who have worked and make Linux portable to a new platform, as well as supporting the user community who have diverse needs and also users can participate act as its own developer team.
1.3 The fundamental difference Linux
One thing that distinguishes Linux to other operating systems is price. Linux is cheaper and can be copied and redistributed without having to pay a fee or royalty to someone. But there are other things more important in addition to price considerations, namely the source code. Linux source code is available to all
people so that everyone can get involved directly in its development. This freedom has allowed hardware vendors make driver for a particular device without having to obtain a license source code that is expensive or menandatanganiNon Disclosure Agreement (NDA). And it also has to provide the possibility for everyone to look into a real operating system and commercial quality. Because Linux is freely available on the internet, various vendors have made a distrbusi package which can be regarded as a packaged version of Linux. This package includes the complete Linux environment, the software for installation and may include specialized software and dedicated support.
1.4 Comparison of Linux to other operating systems
Linux is based on POSIX operating system standard that actually derived based on the work function of UNIX. UNIX is compatible with Linux at the system call level, this means that the majority of programs written for UNIX or Linux can be recompiled and run on other systems with minimal changes. Generally speaking, Linux runs faster than other Unix on the same hardware. And again UNIX has a weakness that is not free.
MS-DOS has similarities with Linux is a file system that is hierarchical. But MS-DOS can only run on x86 processor and does not support multi-user and multi-tasking, as well as non-free. MSDOS also do not have good support in order to interoperate with other operating systems, including the unavailability of network software, program developers and utility programs that exist in Linux. C Compiler uses gcc from the Free Software Foundation's GNU Project. The compiler is widely used in the environment Hewlett-Packard and Sun. Nowadays, a lot of Linux applications that can be used for office purposes such as for spreadsheets, word processor, database and graphics editor program that has the function and look like Microsoft Office, that Star Office. In addition, Corel version is also available for Linux and applications like Matlab on Linux known as Scilab. Linux can be found in a variety of distribution (often called distributions). Distro is a bundle of the Linux kernel, along with a basic Linux system, the installation program, basic tools, and other programs that are useful in accordance with the purpose of making distributions.
There are so many Linux distributions, including:
RedHat, the most popular distributions, minimal in Indonesia. RedHat is the first distribution installation and easy operation.
Debian, the distribution that promotes stability and reliability, even at the expense aspects of ease and sophistication of the program. Debian uses the .deb package installation program.
Slackware, an ever dominate distribution in the Linux world. Almost all Linux documentation is based on Slackware. Two important things on Slackware is that all its content (kernel, library or application) is already proven. So it may be a bit old but certainly stable. The second because he advocated for installing from source so that every program that we install optimized with our system. It's the reason he did not want to use the binary RPM and up to Slackware 4.0, it still uses the libc5 not glibc2 like the others.
SuSE, the distribution of which is very famous with YaST (Yet another Setup Tools) to configure the system. SuSE is the first distribution in which the installation can use the Indonesian language.
Mandrake, RedHat distro is a variant optimized for Pentium. If we use a pentium computer up, generally Linux can walk faster with Mandrake.
WinLinux, distributions are designed to be installed on top of the DOS partition (WIndows). So to run it can be clicked from Windows. WinLinux made as if it is an application program under Windows. And many other distros that are already available or will appear.
1.5 Advantages of Linux
Here are described some advantages of the operating system Linux / UNIX compared to other operating systems. And the following are some of the facts of the things that benefit by using the programs and files of Linux / UNIX:
Basically, all the data stored in the hard disk even if there are some conditions where data is stored on a floppy disk.
Linux / UNIX provides some special process where terminals, printers and other hardware devices can be accessed as we access files stored on the hard disk or diskette.
When the program starts, the program is run from the hard disk into RAM and after the run will be named as the process.
Linux / UNIX provides service to create, modify programs, processes and files.
Linux / UNIX supports hierarchical file structure.
Linux / UNIX operating system is one that belongs to the class of operating systems that can perform multitasking. Multitasking itself is a state in which an operating system can do a lot of work at the same time.
In addition to multitasking, Linux / UNIX also supports multiuser. Namely the operating system at the same time can be used by more than one user is entered into the system. Even for Linux also supports to multiconsole where at the same time in front of computers directly without having to go through the network and allows more than one user entered into the system dakam.
Section 1.6 operating system
Operating System Linux / UNIX consists of the kernel, system program and several application programs. The kernel is the core of the operating system that regulates the use of memory, input output devices, processes, user files on the file system and others. The kernel also provides a set of services that are used to access the so-called kernel system call. System call is used to implement the various services required by the operating system.
System program and all other programs that run on top of the kernel is called user mode. The fundamental difference between the system program and application programs are programs that the system needed an operating system can be run while the application program is a program that is needed to run a particular application.
Example: daemon is a system and word processing program (word processor) is an application program.
1.7 Structure software linux
a. Kernel
The kernel is the most important part of the operating system Linux, which serves as the controller hardware and formed various functions at a low level. The kernel also in the service date, time, file management, security surveillance, process scheduling, memory management, system management, and error handling and intrupsi. Linux kernel consists of several important parts, such as process management, memory management, hardware device drivers, file system drivers, network management and others. But the most important part is the process management and memory management. Memory management to handle local memory consumption, swap area, parts of the kernel and for the buffer cache. Management process to handle the manufacturing processes and scheduling processes. At the base of the kernel contains a hardware device
b. Shell
Shell can be said as a translator in linux which serves to menyembatani between users of the system, meaning that the user simply provides the command and the shell will handle the next action. There is a built-in commands and external commands, built-in command is an internal command being owned by the shell itself being an external command, was the internal shell command outside the command itself. This command can be either utility or application program. There are three types of shell, among others bourne shell program name is sh, C program named csh shell, and Korn shell program called ksh.
c. Utilities
Utilities are small programs that are used to carry out certain tasks. Among others: to process files and directories, editor, communications and networking, system administration, analyzing the work system and others.
d. Program applications
Is a program that is ready to be used by users to meet their own needs. These programs are made with high tinggkat programming language.
CHILDREN 12 YEARS OF STEERING THE SHIP ROHINGYA
CHILDREN 12 YEARS OF STEERING THE SHIP ROHINGYA
A 12-year-old boy Rohingya are believed to drive a ship carrying hundreds of refugees from Myanmar and Bangladesh. He along with hundreds of other refugees were rescued from the damaged vessel in the waters of East Aceh. Is Attaurahman who claims as reported by CNN Indonesia, Thursday (21/5), believed by the captain from Thailand to steer the ship. The shelter region Bayeun Biren, Attaurahman said she initially believed to distribute rice to the hundreds of Rohingya refugees and Bangladesh on the way from Myanmar toward Thailand.
"Captain dear to me. Because I distribute rice, my free entry into the wheelhouse and see how they took it. I then, and one other adult, believed to drive it, "said Attaurahman. The testimony of the other refugees said, after arriving in Thailand they were not allowed to step on the land and remain on the ship for about a month. On the way to Thailand, said Attaurahman, there are eight vessels. A total of 500 people on board they are divided and transferred to four ships, while four other vessels were taken by the captain and crew.
"The captain called two people, me and an adult. He told how to operating this ship, "said Attaurahman that since the child was asked to be captain. The captain and the crew then left the ship. For about 3 months they oscillate at sea before being found by a fisherman.
Attaurahman recognition is justified by other Rohingya refugees. Based on this experience, Attaurahman claimed to aspire to be a sailor when I grow up. "I want to be the driver of the boat," he said. Other witnesses, Hasan Ali, said that in the middle of the ocean coming five people from Myanmar, bringing food and drinks in exchange for part of the ship's engine.
"The engine is removed, gasoline was also taken. Exchanged with rice, water, chili and salt, "said Hasan. Their vessels are not allowed to move closer to Thailand and Bangladesh. Aid from these two countries only a potluck meal, thrown from over the sea. Supply thin, Hasan and Attaurahman together more than 380 other refugees only eat once a day, drink twice a day.
"There is a kitchen on board, to cook the rice and salt. Instant noodles we eat raw without cooking, "said Hasan. Thousands of Rohingya are now housed in several locations in Aceh. Most arrived last week when their boat reached shore Lhokseumawe and Langsa.
"Captain dear to me. Because I distribute rice, my free entry into the wheelhouse and see how they took it. I then, and one other adult, believed to drive it, "said Attaurahman. The testimony of the other refugees said, after arriving in Thailand they were not allowed to step on the land and remain on the ship for about a month. On the way to Thailand, said Attaurahman, there are eight vessels. A total of 500 people on board they are divided and transferred to four ships, while four other vessels were taken by the captain and crew.
"The captain called two people, me and an adult. He told how to operating this ship, "said Attaurahman that since the child was asked to be captain. The captain and the crew then left the ship. For about 3 months they oscillate at sea before being found by a fisherman.
Attaurahman recognition is justified by other Rohingya refugees. Based on this experience, Attaurahman claimed to aspire to be a sailor when I grow up. "I want to be the driver of the boat," he said. Other witnesses, Hasan Ali, said that in the middle of the ocean coming five people from Myanmar, bringing food and drinks in exchange for part of the ship's engine.
"The engine is removed, gasoline was also taken. Exchanged with rice, water, chili and salt, "said Hasan. Their vessels are not allowed to move closer to Thailand and Bangladesh. Aid from these two countries only a potluck meal, thrown from over the sea. Supply thin, Hasan and Attaurahman together more than 380 other refugees only eat once a day, drink twice a day.
"There is a kitchen on board, to cook the rice and salt. Instant noodles we eat raw without cooking, "said Hasan. Thousands of Rohingya are now housed in several locations in Aceh. Most arrived last week when their boat reached shore Lhokseumawe and Langsa.
How Make Array of Age in C Programming
How Make Array of Age in C Programming
Goodnight makers identical program which you like myself that do not have a spouse, but to live with your own computer, on this occasion I have spare time to make a little post which had long I do not do stuff like usual. Okay, now I will share some simple coding of the array in the C programming Direct codingnya see for yourself below!
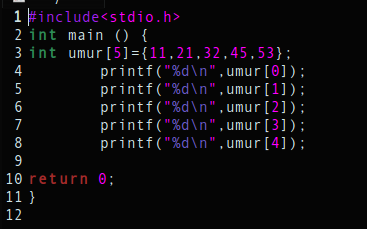
int main () An indication in the program menu.
int umur [5]={11,21,32,45,53}; An array variable declaration of umur.
printf a command to display the output of umur.
return 0; the end of the program if the program runs successfully.
Okay, just so I created this program that I just recently learned of this only campus. If you have questions please filed in the comment column because there is still a lot of knowledge that I have not been able to and also the addition of a science for me and you who where in the learning process. Thank you!
int main () An indication in the program menu.
int umur [5]={11,21,32,45,53}; An array variable declaration of umur.
printf a command to display the output of umur.
return 0; the end of the program if the program runs successfully.
Okay, just so I created this program that I just recently learned of this only campus. If you have questions please filed in the comment column because there is still a lot of knowledge that I have not been able to and also the addition of a science for me and you who where in the learning process. Thank you!
Langganan:
Postingan (Atom)
Popular Posts
-
How to Install Blogger Aceh Widget Your View Blogger Logo Aceh in the Upper Right Corner This blog ?? no? it is not true, because I did...
-
Goodnight makers identical program which you like myself that do not have a spouse, but to live with your own computer, on this occasion I h...
-
add a screensaver on ubuntu many obstacles that were found in the linux-cause an operating system that many people say is not user friend...
-
Are in the Windows operating system or application software acquired open source that can be used? sometimes often we get from some lay peop...
-
Goodnight all rogues! This has been a long time I did not post my personal touch too many tasks to be completed. On this night I'll pos...
Xcrash. Diberdayakan oleh Blogger.